-
Notifications
You must be signed in to change notification settings - Fork 5.4k
Create security/scams learn page #3872
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
 wackerow
left a comment
wackerow
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@minimalsm Thank you for getting this rolling again! Awesome progress here... I know this is still in draft mode, but took a peak and made a handful of comments on the first half that focuses on password management.
This video (https://youtu.be/m8jlnZuV1i4) by Andreas Antonopoulos covers a ton of information related to everything on this page, and imo should be linked to somewhere.
Happy to chat through anything if you have questions. Solid work so far!
src/content/security/index.md
Outdated
|
|
||
| Over 80% of account hacks are a result of weak or stolen passwords. A long combination of characters, numbers and symbols is best to keep your accounts secure. | ||
|
|
||
| A common mistake individuals make is using a long combination of common dictionary words. Passwords like this are insecure because they are prone to a simple hacking technique known as a [dictionary attack](<[https://en.wikipedia.org/wiki/Dictionary_attack](https://en.wikipedia.org/wiki/Dictionary_attack)>). |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Would argue this is heavily dependent on the words used, and how many.
This technique is the basis for BIP-39 (mnemonic seed phrases for key generation in HD wallets). BIP-39 uses a standardized library of 2^11 (2024) words, and when you use 12 random words from this list, it is immensely secure.
Using this approach for the master password of a password manager can be very strong*, and still memorizable by the user. (* Words need to be as RANDOM as possible to be most effective, and more than just a couple words)
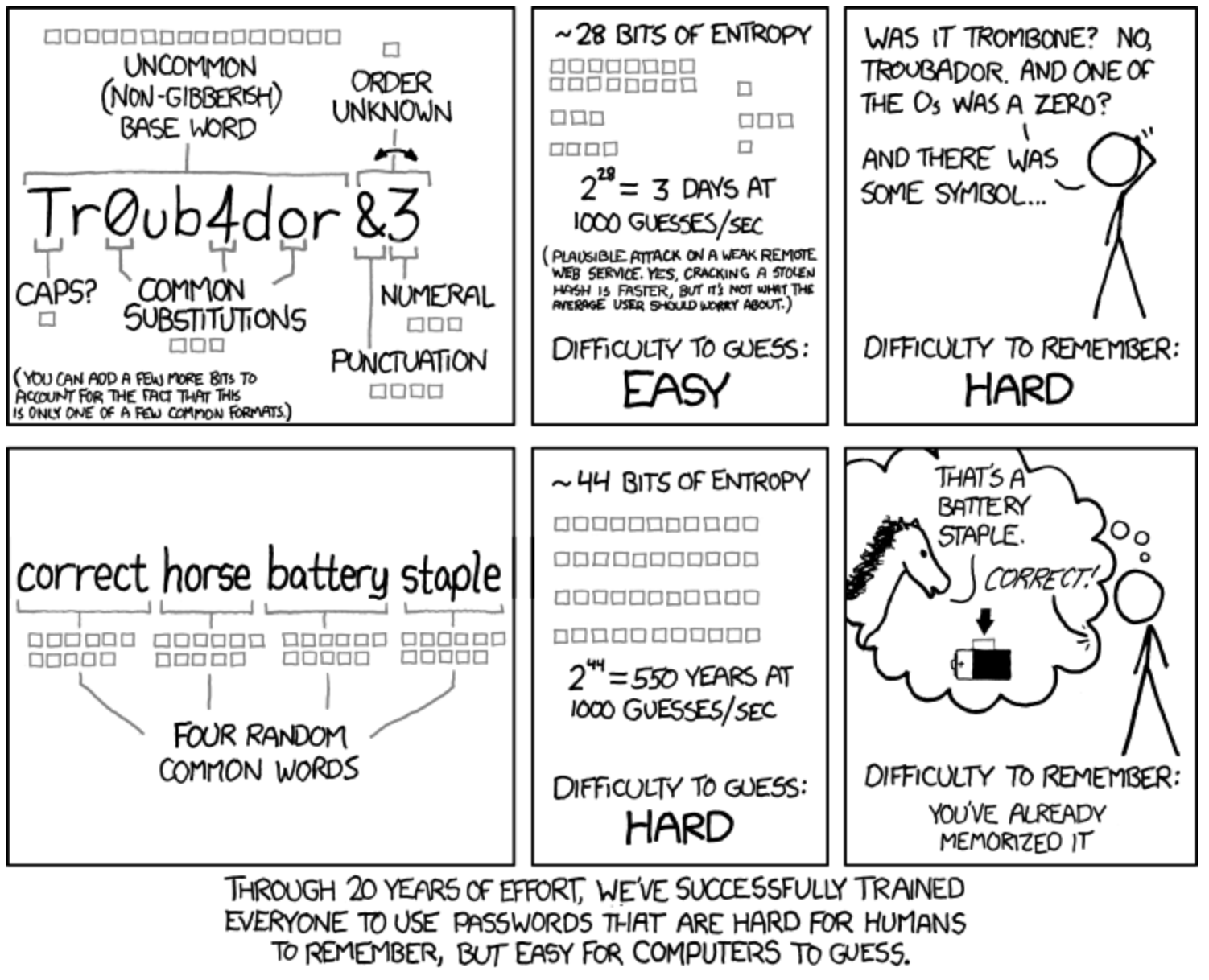
See https://xkcd.com/936/
See https://youtu.be/m8jlnZuV1i4?t=2997 (Andreas Antonopoulos talk - timestamped to the relevant point, but this whole video is full of valuable information related to this topic)
A random string of 8 completely random words from a large dictionary would be quite difficult to break, even with a rainbow attack (especially if salted, like password managers such as Bitwarden use), yet still memorizable and can be typed without difficulty.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Yeah I kinda missed the point I was making. Fixed to say this:
A common mistake individuals make is using a combination of two to three common, related dictionary words. Passwords like this are insecure because they are prone to a simple hacking technique known as a dictionary attack.
I think all of the information you suggested is probably suitable for an advanced section. Happy to iterate on this with you because you're definitely more knowledgeable.
src/content/security/index.md
Outdated
|
|
||
| A strong password doesn't provide as much protection if the password is revealed in a data breach. The website [Have I Been Pwned](<notion://www.notion.so/efdn/%5B%3Chttps://haveibeenpwned.com/%3E%5D(%3Chttps://haveibeenpwned.com/%3E)>) allows you to check if your accounts were involved in any data breaches stored in their database. If they have, **you should change pwned passwords immediately**. Using unique passwords for every account lowers the risk of hackers getting access to all of your accounts when one of your passwords is compromised. | ||
|
|
||
| ### Use a password manager |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This should be #1, and the other three points should be contained within it.
A password manager is 100% essential in my opinion, and by using one, all three of the above points are accomplished pretty much by default (unique strong passwords for every account, no need to memorize anything but your master password).
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Hmmm. If a user takes nothing else from this page other than downloading a password manager it's probably a win. I've added some emphasis to this section to push that.
At the same time, I think going through this should be a linear journey. (i.e. IRL people learn to use symbols and numbers before they make the jump to password managers). Unfortunately, a lot of people won't download a pw manager because of the overhead, I'm not sure moving this to position #1 helps that.
I'm kinda on the fence here - can we discuss this more at standup @wackerow? Would love some other opinions on this.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think you both have good points here. Will do some thinking about it.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@minimalsm Since you've mentioned the costs connected with password managers, would it also make sense to mention which ones offer free plans? I know LastPass and Bitwarden do, while KeePass seems to be completely free.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Since you've mentioned the costs connected with password managers, would it also make sense to mention which ones offer free plans? I know LastPass and Bitwarden do, while KeePass seems to be completely free.
@lukassim sorry I meant cognitive overhead — “how many logical connections or jumps your brain has to make in order to understand or contextualize the thing you’re looking at.”
But good idea we should work out a fair way to differentiate them based on price.
Co-authored-by: Paul Wackerow <[email protected]>
Co-authored-by: Paul Wackerow <[email protected]>
 corwintines
left a comment
corwintines
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Some initial comments on first pass. Looking good so far.
src/content/security/index.md
Outdated
|
|
||
| ## Common Scams | ||
|
|
||
| Todo: add copy here |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think we should mention something about rugpulls here too given the prominence of influencers promoting scam coins. Ex: Kim Kardashian and Floyd Mayweather promoting Ethereum Max. Dont have to call out specific ones to stay neutral, but I think bringing light on this kind of scam wouldn't hurt.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Good point. "Do your own research" is annoying but always useful advice. In this space you can't always rely on a "credible" person or organization to tell you what to do.
Co-authored-by: Corwin Smith <[email protected]>
Co-authored-by: Corwin Smith <[email protected]>
Co-authored-by: Corwin Smith <[email protected]>
Co-authored-by: Corwin Smith <[email protected]>
|
|
||
| Accidently sending crypto to the wrong wallet address is a common mistake. Unless you know the address owner, there will be no way for you to retrieve your funds. | ||
|
|
||
| Always make sure the address you are sending to exactly matches the desired recipient's address before sending a transaction. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Might be a worthy time to recommend ENS (or wallets that provide that, like Argent) to avoid the fat finger address problem?
Co-authored-by: Sam Richards <[email protected]>
Co-authored-by: Sam Richards <[email protected]>
Co-authored-by: Sam Richards <[email protected]>
Co-authored-by: Sam Richards <[email protected]>
| Example of a strong password: ymv\*azu.EAC8eyp8umf | ||
| ``` | ||
|
|
||
| Another common mistake is using passwords that can be easily guessed or found out through [social engineering](<https://en.wikipedia.org/wiki/Social_engineering_(security)>). Including your mother's maiden name, the name's of your children or pets, or dates of birth in your password is not secure and will increase the risk of your password getting hacked. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I found a non-wiki article about social engineering. It does self advertise a bit at the end but otherwise it looks good.
 samajammin
left a comment
samajammin
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Awesome work!
Co-authored-by: Sam Richards <[email protected]>
Co-authored-by: Sam Richards <[email protected]>
Co-authored-by: Sam Richards <[email protected]>
Co-authored-by: Sam Richards <[email protected]>
 wackerow
left a comment
wackerow
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Loving this and keeps getting better... Left a few more comments.
One other thought I had (feel free to ignore) would be a brief note about security on centralized exchanges. Many people get frustrated with the security measures put in place by better exchanges. This stuff may be "annoying" but it's all for the protection of the user. If a user is asked to verify their identity (beyond password/TOTP) using something like their email, or in some cases a selfie, this typically signals increased security, and makes it that much more protected from theft.
Sadly a large number of people leave their keys with exchanges, and if they do, personally would recommend maxing out the security options offered by these exchanges. (ie. use vaults, whitelists, 2FA, etc wherever/whenever feasible)
Otherwise this is all looking awesome! Stoked to get this information published 💪🏻
| ### Use a hardware wallet {#use-hardware-wallet} | ||
|
|
||
| A hardware wallet provides offline storage for private keys. They are considered the most secure wallet option for storing your private keys. | ||
|
|
||
| Keeping private keys offline massively reduces the risk of being hacked, even if a hacker gets control of your computer. | ||
|
|
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Should we mention mnemonic phrases here? Pretty much all hardware wallets (and most software wallets) utilize BIP-39 now, and this random list of words may be very confusing to those new to the space.
People may not understand the differences/similarities between private keys and a mnemonic, and perhaps a quick note to remind people that these words should be the most guarded data you have in the crypto space. Also, guarding the mnemonic long-term involves more than theft protection, but also protection from natural disasters and damage such as fires/floods/crush/electrical shock (ie. put these words on steel).
Co-authored-by: Paul Wackerow <[email protected]>

Description
Deploy preview: http://deploy-preview-3872--ethereumorg.netlify.app/en/security/
Todo