-
Notifications
You must be signed in to change notification settings - Fork 0
Feat/enable git app #1
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Feat/enable git app #1
Conversation
fix(): small fix for private repos 🐛
# This is the 1st commit message: parent 9b74224 author Andy Augustin <[email protected]> 1672219390 +0100 committer Andy Augustin <[email protected]> 1672592292 +0100 gpgsig -----BEGIN PGP SIGNATURE----- iQGzBAABCAAdFiEEApgnwt2TStNZl6Y9UpE0XzZ/UkgFAmOxu6QACgkQUpE0XzZ/ UkjAzgv/cWh9hE7VLkLM1nVmra945WUkOfWXHnCUnrsOWsxxSOkH1r2mLxZdnWtg BlFc4RciJAB39Nv1WBUt+hGBGOdYWcV1lxgSIpn+vNXd9/5xciEThRk9T1piHj+x xnZU2rW0dLlnEnFlIX1qkKeD+rjclXw46umjMgqwIF0vQSx5cR9y8sDCiqRGg2Fv G/k/xLoQwah0Ve8nwqd6dLwNYXl8cFBfvuZaGV/dt1+5BDl4J5mPYg4trxKx5xnB fTxTQ0G/qOa1OInW04EReJWZwQaGvyx5PqEFk0ESk8MuzFytfVVRCnHwdP/QvLO7 S7Y79wUBAQfHvSlwOgBtlQc5eFOiKoxahUhJIcCMLw1r2+nRjuPAA0j07v6nmjDM sfxyVSpnYnKGAfGrYGboOHuEjqKegKdY3oIQFL/Ivln7kmLxGrFcpQ+QMTEJUsLw 2AB+Yf+tJyQXnx8AiGQRnVlXW3FRCOQhCxK2zXMUpzwAsKcKYNnaKoM6jDN7EzRQ fZrB76EK =yGb3 -----END PGP SIGNATURE----- feat(): make gh auth login conditional for separate source repo token 🚀 style(lint): fix lint issues 🐛 feat(): add PAT 🚀 feat(): add PAT 🚀 feat(): add PAT 🚀 feat(): add PAT 🚀 feat(): add PAT 🚀 feat(): add PAT 🚀 feat(): add PAT 🚀 doc(): update docs 📝 feat(): add option for PAT 🚀 feat(): add option for PAT 🚀 # This is the commit message #2: feat(): add option for PAT 🚀 # This is the commit message #3: feat(): add option for PAT 🚀 # This is the commit message #4: feat(): add option for PAT 🚀 # This is the commit message #5: feat(): add option for PAT 🚀 # This is the commit message #6: trial(): add permissions 🐛
author Andy Augustin <[email protected]> 1672219390 +0100 committer Andy Augustin <[email protected]> 1672592292 +0100 gpgsig -----BEGIN PGP SIGNATURE----- iQGzBAABCAAdFiEEApgnwt2TStNZl6Y9UpE0XzZ/UkgFAmOxu6QACgkQUpE0XzZ/ UkjAzgv/cWh9hE7VLkLM1nVmra945WUkOfWXHnCUnrsOWsxxSOkH1r2mLxZdnWtg BlFc4RciJAB39Nv1WBUt+hGBGOdYWcV1lxgSIpn+vNXd9/5xciEThRk9T1piHj+x xnZU2rW0dLlnEnFlIX1qkKeD+rjclXw46umjMgqwIF0vQSx5cR9y8sDCiqRGg2Fv G/k/xLoQwah0Ve8nwqd6dLwNYXl8cFBfvuZaGV/dt1+5BDl4J5mPYg4trxKx5xnB fTxTQ0G/qOa1OInW04EReJWZwQaGvyx5PqEFk0ESk8MuzFytfVVRCnHwdP/QvLO7 S7Y79wUBAQfHvSlwOgBtlQc5eFOiKoxahUhJIcCMLw1r2+nRjuPAA0j07v6nmjDM sfxyVSpnYnKGAfGrYGboOHuEjqKegKdY3oIQFL/Ivln7kmLxGrFcpQ+QMTEJUsLw 2AB+Yf+tJyQXnx8AiGQRnVlXW3FRCOQhCxK2zXMUpzwAsKcKYNnaKoM6jDN7EzRQ fZrB76EK =yGb3 -----END PGP SIGNATURE----- feat(): make gh auth login conditional for separate source repo token 🚀 style(lint): fix lint issues 🐛 feat(): add PAT 🚀 feat(): add PAT 🚀 feat(): add PAT 🚀 feat(): add PAT 🚀 feat(): add PAT 🚀 feat(): add PAT 🚀 feat(): add PAT 🚀 doc(): update docs 📝 feat(): add option for PAT 🚀 feat(): add option for PAT 🚀 feat(): add option for PAT 🚀 feat(): add option for PAT 🚀 feat(): add option for PAT 🚀 feat(): add option for PAT 🚀 trial(): add permissions 🐛 trial(): new trial for accessing private repo with PAT 🆙 trial(): new trial for accessing private repo with PAT 🆙 trial(): new trial for accessing private repo with PAT 🆙 trial(): new trial for accessing private repo with PAT 🆙 trial(): new trial for accessing private repo with PAT 🆙 trial(): new trial for accessing private repo with PAT 🆙 trial(): new trial for accessing private repo with PAT 🆙 trial(): new trial for accessing private repo with PAT 🆙
d05baaf to
a06016d
Compare
|
Hi @AndreasAugustin. This PR had conflicts - I merged and rebased your main branch now - could you solve the last conflicts in your branch or point me out the necessary changes to cherry-pick? |
…it_app Signed-off-by: andy Augustin <[email protected]>
done |
Signed-off-by: andy Augustin <[email protected]>
Signed-off-by: andy Augustin <[email protected]>
|
@msiebeneicher hopefully this is now resolving your feature request. |
src/entrypoint.sh
Outdated
| if [[ -n "${SSH_PRIVATE_KEY_SRC}" ]] &>/dev/null; then | ||
| ssh_setup | ||
| else | ||
| # gh auth login --git-protocol "https" --hostname "${SOURCE_REPO_HOSTNAME}" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
not working, if GITHUB_TOKEN env variable is set, the command throws.
@msiebeneicher is it possible that you use another gh version? I do not understand why this is happening
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
The order here looks mandatory. Also it is not possible to use gh auth status here because gh wants to check a github.com auth by default which is not possible in a github enterprise setup. A working solution for my setup is this:
else
git config --global "credential.https://${SOURCE_REPO_HOSTNAME}.helper" "!gh auth git-credential"
gh auth login --git-protocol "https" --hostname "${SOURCE_REPO_HOSTNAME}" --with-token <<< "${GITHUB_TOKEN}"
fiThere was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
related to docs gh auth status should also work on other hosts (GitHub enterprise), but seems not?
Related to your working solution
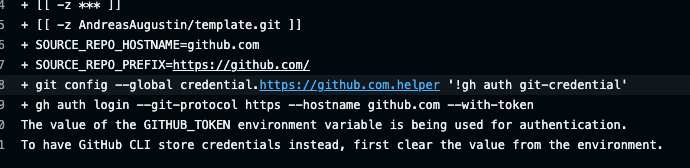
n. Sad but it does not work on github.com https://github.com/AndreasAugustin/actions-template-sync/actions/runs/3823961230/jobs/6505672841
hmmm if it is not a gh --version issue, I guess it is a runner issue (or some magic with the former github app to token action)
Tested on https://github.com/AndreasAugustin/actions-template-sync/tree/chore/auto_test_2
with

Update
we need to change gh auth status --hostname <hostname>
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
aha! maybe the hostname is the issue. Related to https://cli.github.com/manual/gh_help_environment
GH_TOKEN, GITHUB_TOKEN (in order of precedence): an authentication token for github.com API requests. Setting this avoids being prompted to authenticate and takes precedence over previously stored credentials.
It states there explicitly github.com.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
UPDATE
confirmed! It is the hostname variable
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@msiebeneicher with the changes I just made, the tests are working within github.com. Can you please test them in your env?
Hopefully finally it is a working solution!
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
The last solution works also in my environment 🥳
good catch! Do you want to clean up the code before merge?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
The last solution works also in my environment partying_face good catch! Do you want to clean up the code before merge?
think the code is cleaned up, but I will check.
That was a funny and hard issue...
Signed-off-by: andy Augustin <[email protected]>
Signed-off-by: andy Augustin <[email protected]>
we need to remove this line also |
Signed-off-by: andy Augustin <[email protected]>
ad14823
into
msiebeneicher:feat/use_gh_auth_for_authentication
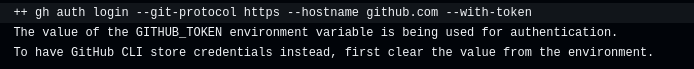
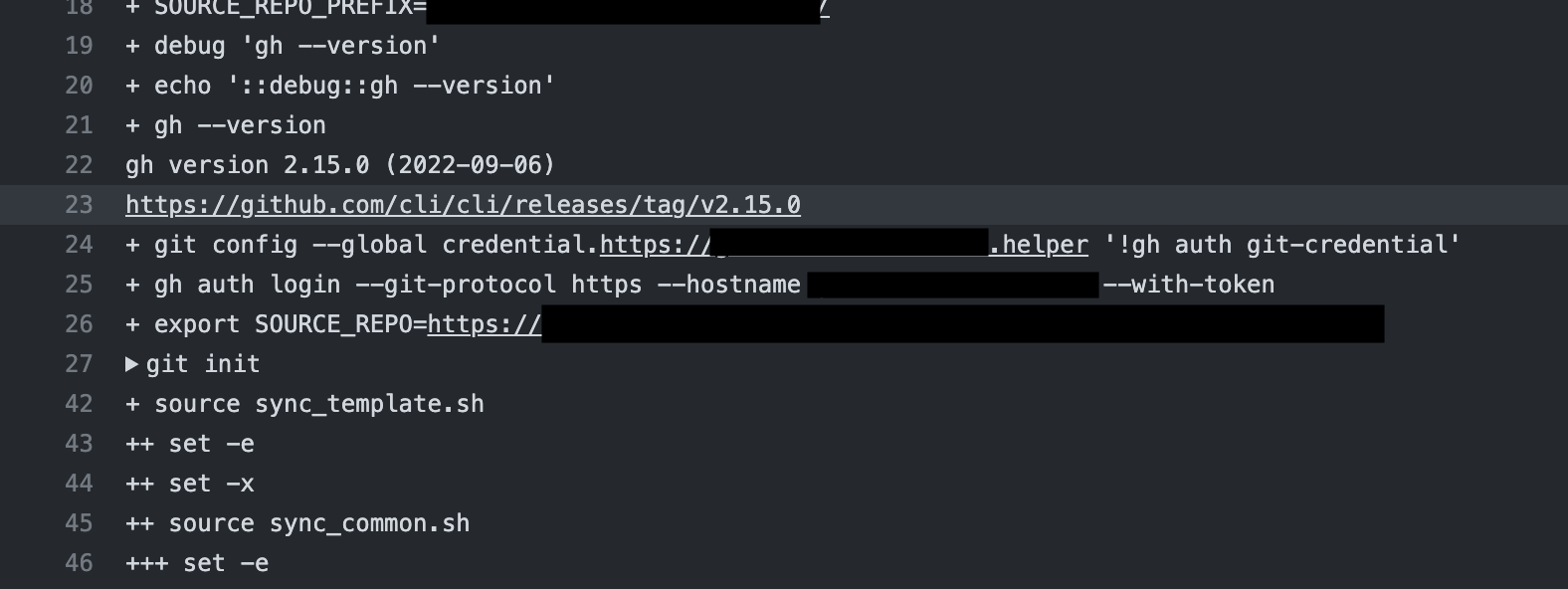
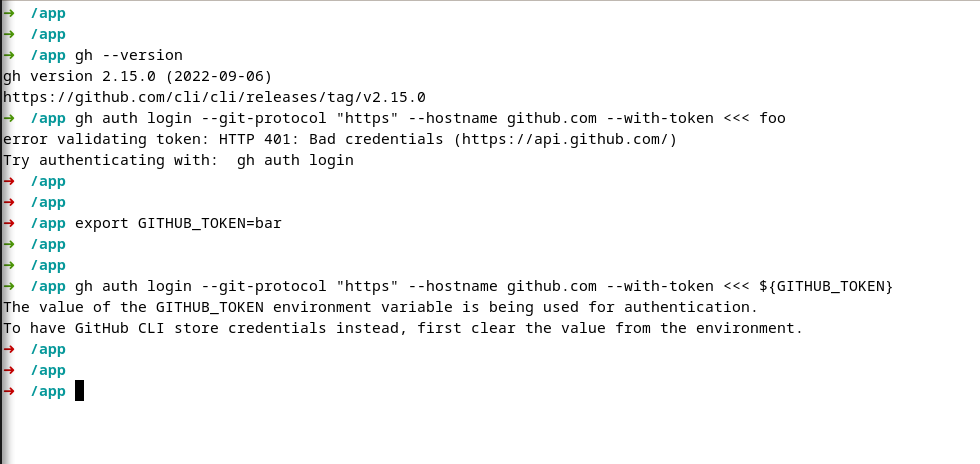
Description
Hi @msiebeneicher could you please review the solution and test in your setup?
It is working with a PAT if the source repository is public. I was not able to make it work with a private repoitory.
Funny details:
Remark
For automation please see closing-issues-using-keywords